Cisco VPN Concentrator 3000
Contents
- 1 Platform Notes
- 2 Version History
- 3 Backoff Patterns
- 4 Vendor IDs
- 5 Authentication Methods
- 6 ISAKMP SA Lifetime
- 7 Transform Attribute ordering and re-writing
- 8 Aggressive Mode
- 9 Response to Noncompliant and Malformed Packets
- 10 NAT Traversal
- 11 IVEv2
- 12 Remote Access VPN Client
- 13 vpnc - client for cisco vpn concentrator
- 14 Other Interesting Behaviour
- 15 Default Configuration
- 16 Discovered Vulnerabilities
Platform Notes
The Cisco VPN Concentrator 3000 was originally an Altiga Networks product. Cisco acquired Altiga in 2000. The Altiga products were called C5, C15 Etc. These were re-badged as the Cisco VPN Concentrator 3005, 3015 Etc.
There are six models: 3005, 3015, 3020, 3030, 3060 and 3080. The 3005 performs all encryption in software; the higher models include slots for hardware encryption modules (SEP and SEP-E) and can also accommodate more memory.
The Cisco VPN Concentrator 3000 runs the pSOS+ operating system on a Motorola CPU. It uses an industry-standard Compact Flash card to store the operating system and configuration.
Cisco VPN Concentrators are often used for high volume remote access VPNs. The high-end models can support hundreds of IPsec tunnels.
IPsec with IKE is enabled by default.
An End-of-Life announcement for the Cisco VPN concentrator was posted on Feb 2007, the end of sale date will be Aug 2007.
Version History
| Version | Release Date | Notes |
|---|---|---|
| 3.5 | ||
| 3.6 | AES Encryption and DH group 5 introduced | |
| 4.0 | SEP-E encryption module support introduced | |
| 4.1 | WebVPN introduced | |
| 4.7 | Mar 2005 | SSL VPN and Cisco Secure desktop introduced |
Software versions 3.5, 3.6 and 4.0 are obsolete now.
Because the Cisco VPN Concentrator 3000 will soon be reaching End-of-Life, it is expected that 4.7 will be the last software release for this platform.
Unless mentioned otherwise, the examples below are from a Cisco VPN Concentrator 3005 running software version 4.7.2.L
Backoff Patterns
Cisco VPN Concentrator 3000 series has the four-packet backoff pattern:
0, 8, 8, 8
Below is an example backoff pattern from a Cisco VPN Concentrator 3030 running software version 4.7.2E:
$ ike-scan -M --showbackoff 192.168.124.253
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.253 Main Mode Handshake returned
HDR=(CKY-R=92ca87ca7d38b4c7)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
IKE Backoff Patterns:
IP Address No. Recv time Delta Time
192.168.124.253 1 1171889630.344950 0.000000
192.168.124.253 2 1171889638.336474 7.991524
192.168.124.253 3 1171889646.335458 7.998984
192.168.124.253 4 1171889654.334416 7.998958
192.168.124.253 Implementation guess: Cisco VPN Concentrator
Vendor IDs
The Cisco VPN Concentrator sends the following Vendor IDs in the first Main Mode packet:
- 4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
And it sends the following Vendor IDs in the first Aggressive Mode packet:
- 12f5f28c457168a9702d9fe274cc0100 (Cisco Unity)
- 09002689dfd6b712 (XAUTH)
- afcad71368a1f1c96b8696fc77570100 (Dead Peer Detection v1.0)
- 4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
- 4187bd00363672eee05be3a6f95d9528 (Unknown, varies)
- 1f07f70eaa6514d3b0fa96542a500407 (Cisco VPN Concentrator)
Authentication Methods
The Cisco VPN Concentrator 3000 supports the following authentication methods:
- Pre-Shared Key
- RSA Signature
- Hybrid
- XAUTH
Here are examples showing IKE responses with these authentication mechanisms:
$ ike-scan -M --auth=1 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=15ff31044a4a1c2b)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
$ ike-scan -M --auth=3 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=d884567c91171866)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=RSA_Sig LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
$ ike-scan -M --auth=64221 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=6ee4af1bee63e7cd)
SA=(Enc=3DES Hash=SHA1 Group=2:modp1024 Auth=Hybrid LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
$ ike-scan -M --auth=65001 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=0cbf680b099121bf)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=XAUTH LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
ISAKMP SA Lifetime
Here we specify no lifetime attributes, and the concentrator responds without any lifetime attributes in its response.
$ ike-scan -M --lifetime=none 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=dd52d15517592765)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
Here we specify the value 1 for both seconds and kilobytes, and observe both returned.
$ ike-scan -M --lifetime=1 --lifesize=1 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=8c95f40f6172d16f)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=1 LifeType=Kilobytes LifeDuration=1)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
Here is the same thing with the value 0xffffffff. In this case, the concentrator returns the attributes as variable length.
$ ike-scan -M --lifetime=0xffffffff --lifesize=0xffffffff 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=64e8975409759a7f)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration(4)=0xffffffff LifeType=Kilobytes LifeDuration(4)=0xffffffff)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
If we specify values that use more than four bytes, the concentrator does not respond.
$ ike-scan -M --lifetime=0xffffffffffffffff --lifesize=0xffffffffffffffff 192.168.124.152 Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9.1: 1 hosts scanned in 2.502 seconds (0.40 hosts/sec). 0 returned handshake; 0 returned notify
Transform Attribute ordering and re-writing
The Cisco VPN Concentrator always returns transform attributes in the order: Enc [,KeyLength], Hash, Group, Auth [,LifeType=Seconds] [,LifeType=Kilobytes].
$ ike-scan -M --trans="(1=5,2=1,3=1,4=2)" 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=e5b11330e001c63f)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
$ ike-scan -M --trans="(4=2,3=1,2=1,1=5)" 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=70569793dbcb637f)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
$ ike-scan -M --trans="(1=7,4=2,3=1,2=2,14=128)" 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=4db99a8e898c004e)
SA=(Enc=AES KeyLength=128 Hash=SHA1 Group=2:modp1024 Auth=PSK)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
$ ike-scan -M --trans="(14=128,11=1,12=5678,11=2,12=1234,4=2,3=1,2=2,1=7)" 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=d6cca16601d26893)
SA=(Enc=AES KeyLength=128 Hash=SHA1 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=5678 LifeType=Kilobytes LifeDuration=1234)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
Aggressive Mode
The Cisco VPN Concentrator 3000 supports aggressive mode.
The vpn group name is given as the ID. Later versions will respond to any ID to prevent groupname enumeration.
Here is an example aggressive mode response.
$ ike-scan -M -A --id=vpngroup 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Aggressive Mode Handshake returned
HDR=(CKY-R=b4401a1d363772ee)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
KeyExchange(128 bytes)
Nonce(20 bytes)
ID(Type=ID_IPV4_ADDR, Value=192.168.124.152)
Hash(16 bytes)
VID=12f5f28c457168a9702d9fe274cc0100 (Cisco Unity)
VID=09002689dfd6b712 (XAUTH)
VID=afcad71368a1f1c96b8696fc77570100 (Dead Peer Detection v1.0)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
VID=4187bd00363672eee05be3a6f95d9528
VID=1f07f70eaa6514d3b0fa96542a500407 (Cisco VPN Concentrator)
Response to Noncompliant and Malformed Packets
No Acceptable Transforms
The Cisco VPN Concentrator does not respond to unacceptable proposals.
$ ike-scan --trans=1,2,3,4 -M 192.168.124.152 Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9.1: 1 hosts scanned in 2.439 seconds (0.41 hosts/sec). 0 returned handshake; 0 returned notify
Bad IKE version
The Cisco VPN Concentrator does not appear to check the IKE header version.
$ ike-scan -M --headerver=0x30 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=c77b8fba9f5ccf06)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
$ ike-scan -M --headerver=0x11 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=371396a0cfc43399)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
Invalid DOI
No response.
$ ike-scan -M --doi=2 192.168.124.152 Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9.1: 1 hosts scanned in 2.476 seconds (0.40 hosts/sec). 0 returned handshake; 0 returned notify
Invalid Situation
The Cisco VPN Concentrator does not appear to check this.
$ ike-scan -M --situation=2 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=c7e0373fbcd7b850)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
Invalid Initiator Cookie
The Cisco VPN Concentrator does not appear to check this, or perhaps it considers a zero initiator cookie to be valid.
$ ike-scan -M --cookie=0000000000000000 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=f53f64d21edabf67)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
Invalid Flags
No response.
$ ike-scan -M --hdrflags=255 192.168.124.152 Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9.1: 1 hosts scanned in 2.477 seconds (0.40 hosts/sec). 0 returned handshake; 0 returned notify
Invalid Protocol
No response.
$ ike-scan -M --protocol=2 192.168.124.152 Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9.1: 1 hosts scanned in 2.477 seconds (0.40 hosts/sec). 0 returned handshake; 0 returned notify
Invalid SPI
The Cisco VPN Concentrator does not appear to check this.
$ ike-scan -M --spisize=32 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=4d577515f3b6bac6)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
Non-Zero Reserved Fields
The Cisco VPN Concentrator does not appear to check this.
$ ike-scan -M --mbz=255 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=e5da74bd1eeded4b)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
NAT Traversal
The Cisco VPN Concentrator supports NAT traversal.
$ ike-scan --nat-t -M 192.168.124.152
Starting ike-scan 1.9.1 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.152 Main Mode Handshake returned
HDR=(CKY-R=cd61180deb15b4dd)
SA=(Enc=3DES Hash=MD5 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
VID=4048b7d56ebce88525e7de7f00d6c2d3c0000000 (IKE Fragmentation)
IVEv2
The Cisco VPN Concentrator 3000 series does not support IKEv2 as of version 4.7.2.L.
Remote Access VPN Client
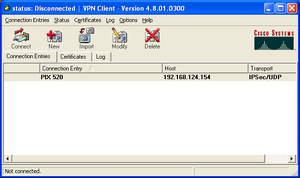
The Cisco VPN Concentrator uses the Cisco VPN client for remote access connections. This client is also used for VPN connections to other Cisco VPN products including IOS (used on Cisco routers) and Cisco PIX. This VPN client is sometimes known as the Cisco Unity Client.
The Cisco VPN client supports Windows, MacOS, Linux and Solaris. The screenshot on the right shows version 4.8.01 of the Windows client running on Windows XP.
The VPN client can be configured for either Group authentication, which is a username/password authentication scheme using IKE Pre-Shared Key authentication (possibly with a later XAUTH authentication step to provide secondary user-level authentication), or Certificate Authentication.
Cisco VPN Client version 4.8.01 offers the following fourteen transforms in order using group authentication:
| No. | Encryption | Hash | Authentication | DH Group | Lifetime (Seconds) |
|---|---|---|---|---|---|
| 1 | AES/256 | SHA1 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 2 | AES/256 | MD5 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 3 | AES/256 | SHA1 | PSK | 2 (MODP 1024) | 2,147,483 |
| 4 | AES/256 | MD5 | PSK | 2 (MODP 1024) | 2,147,483 |
| 5 | AES/128 | SHA1 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 6 | AES/128 | MD5 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 7 | AES/128 | SHA1 | PSK | 2 (MODP 1024) | 2,147,483 |
| 8 | AES/128 | MD5 | PSK | 2 (MODP 1024) | 2,147,483 |
| 9 | 3DES | SHA1 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 10 | 3DES | MD5 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 11 | 3DES | SHA1 | PSK | 2 (MODP 1024) | 2,147,483 |
| 12 | 3DES | MD5 | PSK | 2 (MODP 1024) | 2,147,483 |
| 13 | DES | MD5 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 14 | DES | MD5 | PSK | 2 (MODP 1024) | 2,147,483 |
For the authentication methods, PSK is Pre-Shared Key (value 1), and XAUTH is XAUTH Init PreShared (value 65001).
This corresponds to the following proposal: ((AES/256 or AES/128 or 3DES) and (SHA1 or MD5) and (XAUTH or PSK) and Group2) or (DES and MD5 and (XAUTH or PSK) and Group2).
The lifetime of 2,147,483 seconds is a mystery. This corresponds to a SA lifetime of about 24 days, which is an absurdly large value.
It also sends five Vendor ID payloads:
- XAUTH (09002689dfd6b712)
- Dead Peer Detection v1.0 (afcad71368a1f1c96b8696fc77570100)
- IKE Fragmentation (4048b7d56ebce88525e7de7f00d6c2d380000000)
- draft-ietf-ipsec-nat-t-ike-02\n (90cb80913ebb696e086381b5ec427b1f)
- Cisco Unity (12f5f28c457168a9702d9fe274cc0100)
The DHGroup keyword can be used in the .pcf profile file (tested with Cisco VPN Client version 5.0.04.0300) to override the default DH Group 2. When adding the line DHGroup=5 in the .pcf file, Cisco VPN Client version 5.0.04.030 offers the following four transforms in order using group authentication:
| No. | Encryption | Hash | Authentication | DH Group | Lifetime (Seconds) |
|---|---|---|---|---|---|
| 1 | AES/128 | SHA1 | XAUTH | 5 (MODP 1536) | 2,147,483 |
| 2 | AES/128 | MD5 | XAUTH | 5 (MODP 1536) | 2,147,483 |
| 3 | AES/128 | SHA1 | PSK | 5 (MODP 1536) | 2,147,483 |
| 4 | AES/128 | MD5 | PSK | 5 (MODP 1536) | 2,147,483 |
No IKE Proposals will match by default on a VPN Concentrator 3000 version 4.7.2.O, a new IKE Proposal must be manually added, something like CiscoVPNClient-AES128-SHA-DH5, and activated. To be completely coherent, a new SA must be created, something like ESP-AES128-SHA-DH5, and selected in the Group (IPSec tab, IPSec SA field).
vpnc - client for cisco vpn concentrator
vpnc is a vpn client compatible with the Cisco VPN Concentrator 3000, it is distributed under GPL licence. The home page of vpnc is http://www.unix-ag.uni-kl.de/~massar/vpnc/
vpnc is supposed to work with Cisco VPN concentrator 3000 Series, Cisco IOS routers, Cisco PIX / ASA Security Appliances and Juniper/Netscreen. The supported platforms are Linux (i386/ppc/zaurus tested), NetBSD (i386 tested), FreeBSD (CURRENT of 23.11.2003 tested), OpenBSD (CURRENT of 18.04.2004 tested), DragonFly BSD, Darwin / Mac OS X, Solaris (7 works, 9 only with --natt-mode forced) and Windows / Cygwin.
vpnc version 0.5.3 (compiled on Ubuntu 9.04 Jaunty) offers the following 24 transforms in order using group authentication:
| No. | Encryption | Hash | Authentication | DH Group | Lifetime (Seconds) |
|---|---|---|---|---|---|
| 1 | AES/256 | SHA1 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 2 | AES/256 | MD5 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 3 | AES/192 | SHA1 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 4 | AES/192 | MD5 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 5 | AES/128 | SHA1 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 6 | AES/128 | MD5 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 7 | 3DES | SHA1 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 8 | 3DES | MD5 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 9 | DES | SHA1 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 10 | DES | MD5 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 11 | RESERVED(0) | SHA1 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 12 | RESERVED(0) | MD5 | XAUTH | 2 (MODP 1024) | 2,147,483 |
| 13 | AES/256 | SHA1 | PSK | 2 (MODP 1024) | 2,147,483 |
| 14 | AES/256 | MD5 | PSK | 2 (MODP 1024) | 2,147,483 |
| 15 | AES/192 | SHA1 | PSK | 2 (MODP 1024) | 2,147,483 |
| 16 | AES/192 | MD5 | PSK | 2 (MODP 1024) | 2,147,483 |
| 17 | AES/128 | SHA1 | PSK | 2 (MODP 1024) | 2,147,483 |
| 18 | AES/128 | MD5 | PSK | 2 (MODP 1024) | 2,147,483 |
| 19 | 3DES | SHA1 | PSK | 2 (MODP 1024) | 2,147,483 |
| 20 | 3DES | MD5 | PSK | 2 (MODP 1024) | 2,147,483 |
| 21 | DES | SHA1 | PSK | 2 (MODP 1024) | 2,147,483 |
| 22 | DES | MD5 | PSK | 2 (MODP 1024) | 2,147,483 |
| 23 | RESERVED(0) | SHA1 | PSK | 2 (MODP 1024) | 2,147,483 |
| 24 | RESERVED(0) | MD5 | PSK | 2 (MODP 1024) | 2,147,483 |
For the authentication methods, PSK is Pre-Shared Key (value 1), and XAUTH is XAUTH Init PreShared (value 65001).
When using "--dh dh5", the DH Group is set to 5 (MODP 1536).
The lifetime of 2,147,483 seconds is the same as the Cisco VPN Client. This corresponds to a SA lifetime of about 24 days, which is an absurdly large value.
vpnc also sends 8 Vendor ID payloads:
- XAUTH (09002689dfd6b712)
- Cisco Unity (12f5f28c457168a9702d9fe274cc0100)
- RFC 3947 Negotiation of NAT-Traversal in the IKE (4a131c81070358455c5728f20e95452f)
- draft-ietf-ipsec-nat-t-ike-02\n (90cb80913ebb696e086381b5ec427b1f)
- draft-ietf-ipsec-nat-t-ike-02 (cd60464335df21f87cfdb2fc68b6a448)
- draft-ietf-ipsec-nat-t-ike-01 (16f6ca16e4a4066d83821a0f0aeaa862)
- draft-ietf-ipsec-nat-t-ike-00 (4485152d18b6bbcd0be8a8469579ddcc)
- Dead Peer Detection v1.0 (afcad71368a1f1c96b8696fc77570100)
Other Interesting Behaviour
IKE over TCP
The Cisco VPN Concentrator 3000 series supports IKE over TCP, although this is not enabled by default. The TCP port is 10000 by default, but this can be changed.
The protocol used is Cisco proprietary, and consists of the entire UDP datagram (including headers) plus some additional data encapsulated within a TCP segment.
Cisco VPN concentrators are the only systems that have been observed to use this encapsulated IKE over TCP, so if you see it then it's almost certainly a VPN concentrator. Checkpoint Firewall-1 also supports IKE over TCP, but it uses a different encapsulation format.
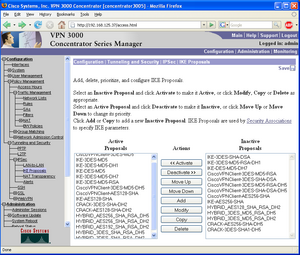
Default Configuration
The default IKE Phase-1 proposals for Version 4.7.2.B as displayed in the command line interface are shown below. The screenshot on the right shows the same list in the web-based GUI.
The Active IKE Proposals ------------------------------------------------------------------------------- | 1. CiscoVPNClient-3DES-MD5 | 2. IKE-3DES-MD5 | | 3. IKE-3DES-MD5-DH1 | 4. IKE-DES-MD5 | | 5. IKE-3DES-MD5-DH7 | 6. IKE-3DES-MD5-RSA | | 7. CiscoVPNClient-3DES-MD5-DH5 | 8. CiscoVPNClient-AES128-SHA | | 9. IKE-AES128-SHA | 10. CRACK-3DES-SHA-DH2 | | 11. CRACK-AES128-SHA-DH2 | 12. HYBRID_AES256_SHA_RSA_DH5 | | 13. HYBRID_AES256_SHA_RSA_DH2 | 14. HYBRID_AES192_SHA_RSA_DH2 | | 15. HYBRID_3DES_SHA_RSA_DH5 | 16. HYBRID_3DES_SHA_RSA_DH2 | -------------------------------------------------------------------------------
The table below shows the Cisco-Supplied Default IKE Proposals that are Active by Default.
| Proposal Name | Authentication Mode | Authentication Algorithm | Encryption Algorithm | Diffie-Hellman Group |
|---|---|---|---|---|
| CiscoVPNClient-3DES-MD5 | Preshared Keys (XAUTH) | MD5/HMAC-128 | 3DES-168 | 2 (1024-bits) |
| IKE-3DES-MD5 | Preshared Keys | MD5/HMAC-128 | 3DES-168 | 2 |
| IKE-3DES-MD5-DH1 | Preshared Keys | MD5/HMAC-128 | 3DES-168 | 1 (768-bits) |
| IKE-DES-MD5 | Preshared Keys | MD5/HMAC-128 | DES-56 | 1 |
| IKE-3DES-MD5-DH7 | Preshared Keys | MD5/HMAC-128 | 3DES-168 | 7 (ECC) |
| IKE-3DES-MD5-RSA | RSA Digital Certificate | MD5/HMAC-128 | 3DES-168 | 2 (1024-bits) |
| IKE-AES128-SHA | Preshared Keys | SHA/HMAC-160 | AES-128 | 2 |
| CiscoVPNClient-AES128- SHA | Preshared Keys | SHA/HMAC-160 | AES-128 | 2 |
| CiscoVPNClient-3DES-MD5-DH5 | 3DES-168 | MD5/HMAC-128 | 3DES-168 | 5 (1536-bits) |
| HYBRID_AES256_SHA_RSA_DH5 | RSA Cert (HYBRID) | SHA/HMAC-160 | AES-256 | 5 |
| HYBRID_AES256_SHA_RSA_DH2 | RSA Cert (HYBRID) | SHA/HMAC-160 | AES-256 | 2 |
| HYBRID_AES192_SHA_RSA_DH2 | RSA Cert (HYBRID) | SHA/HMAC-160 | AES-192 | 2 |
| HYBRID_3DES_SHA_RSA_DH5 | RSA Cert (HYBRID) | SHA/HMAC-160 | 3DES-168 | 5 |
| HYBRID_3DES_SHA_RSA_DH2 | RSA Cert (HYBRID) | SHA/HMAC-160 | 3DES-168 | 2 |
| HYBRID_AES128_SHA_RSA_DH2 | RSA Cert (HYBRID) | SHA/HMAC-160 | AES-128 | 2 |