IBM AIX
Contents
- 1 Platform Notes
- 2 Version History
- 3 Backoff Patterns
- 4 Vendor IDs
- 5 Authentication Methods
- 6 ISAKMP SA Lifetime
- 7 Transform Ordering and Re-Writing
- 8 Aggressive Mode
- 9 Response to Noncompliant and Malformed Packets
- 10 NAT Traversal
- 11 IVEv2
- 12 Remote Access VPN Client
- 13 Other Interesting Behaviour
- 14 Default Configuration
- 15 Discovered Vulnerabilities
- 16 Misc Notes
Platform Notes
AIX is IBM's proprietary Unix. It has supported IPsec VPN since version 4.3, with IKE support being added with software version 4.3.2.
It uses an XML-based configuration file to define VPN tunnels. There are several interfaces to this, including the command line, SMIT and the web-based system management interface.
Version History
| Version | Release Date | Notes |
|---|---|---|
| 4.2.1 | Apr 1997 | |
| 4.3 | Oct 1997 | IPsec support added (manual keying only) |
| 4.3.1 | Apr 1998 | |
| 4.3.2 | Oct 1998 | IKE support added |
| 4.3.3 | Sep 1999 | |
| 5L 5.1 | May 2001 | |
| 5L 5.2 | Oct 2002 | |
| 5L 5.3 | Aug 2004 | NAT Traversal support added |
Backoff Patterns
IBM AIX has the unusual backoff pattern:
0, 16, 32, 64, 128, 128, 256, 512
This is unusual for two reasons:
- It goes on for about nineteen minutes, which is far longer than any other pattern; and
- It has a "hiccup" where it sends two packets with the same backoff and then resumes the doubling pattern.
Because the spacing between the retries exceeds the default ike-scan backoff timeout after the first three packets, ike-scan will only show the first three packets unless the timeout is increased.
Here is a backoff pattern from an RS/6000 system running IBM AIX 5L 5.3 using the default ike-scan backoff timeout:
$ ike-scan -M --showbackoff 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=04455d7b8d26aa9b)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
IKE Backoff Patterns:
IP Address No. Recv time Delta Time
192.168.124.156 1 1173695246.414887 0.000000
192.168.124.156 2 1173695262.646832 16.231945
192.168.124.156 3 1173695294.648068 32.001236
192.168.124.156 Implementation guess: IBM AIX
Here is an example with a large backoff timeout of 4,100 seconds, which shows the entire backoff pattern from the same AIX 5L 5.3 system:
$ ike-scan -M --trans=1,1,1,1 --showbackoff=4100 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=5883fb4c0f586c1d)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
IKE Backoff Patterns:
IP Address No. Recv time Delta Time
192.168.124.156 1 1173708006.525457 0.000000
192.168.124.156 2 1173708022.525299 15.999842
192.168.124.156 3 1173708054.525784 32.000485
192.168.124.156 4 1173708118.526464 64.000680
192.168.124.156 5 1173708246.527520 128.001056
192.168.124.156 6 1173708374.528538 128.001018
192.168.124.156 7 1173708630.530217 256.001679
192.168.124.156 8 1173709142.532943 512.002726
192.168.124.156 Implementation guess: IBM AIX
Vendor IDs
IBM AIX does not return any Vendor IDs in either Main Mode or Aggressive Mode.
The only exception is that AIX will return the RFC 3947 NAT Traversal Vendor ID if it is specified in the initiator's packet.
$ ike-scan -M --trans=1,1,1,1 --vendor=4a131c81070358455c5728f20e95452f 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=ad68c4a5f27768a7)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
VID=4a131c81070358455c5728f20e95452f (RFC 3947 NAT-T)
Authentication Methods
IBM AIX supports Pre-Shared Key and RSA Signature authentication methods, with Pre-Shared Key being the default.
ISAKMP SA Lifetime
IBM AIX supports a lifetime in seconds, a lifetime in kilobytes, or none or both. When a lifetime in seconds or lifetime in kilobytes is specified, the value must be above a certain minimum value.
Lifetime in Seconds
IBM AIX will support either no lifetime in seconds, or a lifetime with a value greater than or equal to 120 seconds (two minutes). If no lifetime is specified, then no lifetime is returned. If a lifetime below 120 seconds is specified, then NO-PROPOSAL-CHOSEN is returned. AIX supports any lifetime in seconds value that is greater than the minimum.
$ ike-scan -M --lifetime=none 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=9905c25b8e2a31b1)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768)
$ ike-scan -M --lifetime=0 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=2cafcf19a7296bbb, msgid=5bff7af1)
$ ike-scan -M --lifetime=1 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=3a95dd3394fa754d, msgid=8e442360)
$ ike-scan -M --lifetime=119 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=6b827c800fd7c6c2, msgid=2c78c3fd)
$ ike-scan -M --lifetime=120 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=0da8177cb91decf2)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00000078)
$ ike-scan -M --lifetime=0xffffffff 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=1e627be567d1acfa)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0xffffffff)
$ ike-scan -M --lifetime=0xffffffffffffffff 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=9170190077cfbea6)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(8)=0xffffffffffffffff)
Lifetime in Kilobytes
IBM AIX supports either no lifetime in kilobytes, or a lifetime with a value greater than or equal to 50 kilobytes. If no lifetime is specified, then no lifetime is returned. If a lifetime below 50 kilobytes is specified, then NO-PROPOSAL-CHOSEN is returned. AIX supports any lifetime in kilobytes value that is greater than the minimum.
$ ike-scan -M --lifetime=none --lifesize=0 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=5d9b46f6fe212eb2, msgid=8cfad24f)
$ ike-scan -M --lifetime=none --lifesize=1 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=fa2a9f7372c674cd, msgid=cb019418)
$ ike-scan -M --lifetime=none --lifesize=49 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=ce48679d28d9698c, msgid=0264ff44)
$ ike-scan -M --lifetime=none --lifesize=50 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=4a51fff3b14c1035)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Kilobytes LifeDuration(4)=0x00000032)
$ ike-scan -M --lifetime=none --lifesize=0xffffffff 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=67bc6245e5a31df5)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Kilobytes LifeDuration(4)=0xffffffff)
$ ike-scan -M --lifetime=none --lifesize=0xffffffffffffffff 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=b8107d1b0d7f1e2f)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Kilobytes LifeDuration(8)=0xffffffffffffffff)
AIX also supports both a lifetime in seconds and a lifetime in kilobytes, providing that the values for both are greater than or equal to the minimums of 120 seconds and 50 kilobytes.
$ ike-scan -M --lifetime=0xffffffff --lifesize=0xffffffff 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=e089af5c24b16fb6)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0xffffffff LifeType=Kilobytes LifeDuration(4)=0xffffffff)
Transform Ordering and Re-Writing
IBM AIX returns the transform attributes in the order that they are sent by the initiator.
$ ike-scan -M --trans="(1=1,2=1,3=1,4=1)" 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=983b1aa10dec7cbe)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768)
$ ike-scan -M --trans="(4=1,3=1,2=1,1=1)" 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=adf9164319a89349)
SA=(Group=1:modp768 Auth=PSK Hash=MD5 Enc=DES)
Aggressive Mode
IBM AIX supports both Main Mode and Aggressive Mode, although Main Mode is the default.
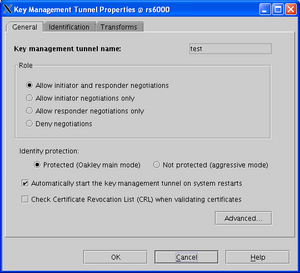
The screenshot on the right shows the general tab of the IKE tunnel properties on IBM AIX 5L 5.3 using the web-based system management interface. You can see the radio buttons to select Main Mode or Aggressive Mode under Identity Protection, labelled Protected (OAKLEY main mode) and Not Protected (aggressive mode).
It is not possible to select both Main Mode and Aggressive Mode, so any tunnel on AIX will support one or the other but not both. We will see later that sending a Main Mode request to a tunnel configured for Aggressive Mode, or an Aggressive Mode request to a Main Mode tunnel will result in a BAD-PROPOSAL-SYNTAX message.
The example below shows an aggressive mode response from an IBM RS/6000 system running AIX 5L 5.3. In this example, we need to specify a custom transform (--trans=1,1,1,1) with a key exchange using Diffie-Hellman group-1 (--dhgroup=1). We also need to use the ID type ID_IPV4_ADDR (--idtype=1) and the ID 192.168.124.7 (--id=0xc0a87c07).
$ ike-scan -A --trans=1,1,1,1 --dhgroup=1 -M --idtype=1 --id=0xc0a87c07 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Aggressive Mode Handshake returned
HDR=(CKY-R=5f6930ebe848b590)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
KeyExchange(96 bytes)
Nonce(8 bytes)
ID(Type=ID_IPV4_ADDR, Value=192.168.124.156)
Hash(16 bytes)
The eight-byte (256-bit) nonce is incredibly short - most systems use either sixteen or twenty bytes (128 or 160 bits) - but it is allowed by RFC 2409 which states: The length of nonce payload MUST be between 8 and 256 bytes inclusive.
IBM AIX will support either Main Mode or Aggressive Mode for each specified tunnel, but not both. If a tunnel is configured for Aggressive Mode, then it will respond to a Main Mode request with BAD-PROPOSAL-SYNTAX as shown below:
$ ike-scan -M 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 15 (BAD-PROPOSAL-SYNTAX)
HDR=(CKY-R=b63a7ef2218ad391, msgid=39163744)
The same behaviour occurs if an Aggressive Mode request is sent to a system configures with a Main Mode tunnel:
$ ike-scan -A --trans=1,1,1,1 --dhgroup=1 -M --idtype=1 --id=0xc0a87c07 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 15 (BAD-PROPOSAL-SYNTAX)
HDR=(CKY-R=75491688ac2e74f9, msgid=a74d8277)
Response to Noncompliant and Malformed Packets
The examples below are from IBM AIX 5L 5.3 running on an RS/6000.
No Acceptable Transforms
$ ike-scan -M --trans=5,1,1,1 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 14 (NO-PROPOSAL-CHOSEN)
HDR=(CKY-R=1e54ed4f615d14e5, msgid=f9fbf64a)
Bad IKE version
$ ike-scan -M --headerver=0x30 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 5 (INVALID-MAJOR-VERSION)
HDR=(CKY-R=e82507a97f89155e, msgid=50804026)
$ ike-scan -M --headerver=0x11 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 6 (INVALID-MINOR-VERSION)
HDR=(CKY-R=8cf923d99de37212, msgid=cee2f3b9)
Invalid DOI
$ ike-scan -M --doi=2 192.168.124.156 Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9: 1 hosts scanned in 2.475 seconds (0.40 hosts/sec). 0 returned handshake; 0 returned notify
Invalid Situation
$ ike-scan -M --situation=2 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=6c6c743f031f992a)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
Invalid Initiator Cookie
$ ike-scan -M --cookie=0000000000000000 192.168.124.156 Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/) Ending ike-scan 1.9: 1 hosts scanned in 2.473 seconds (0.40 hosts/sec). 0 returned handshake; 0 returned notify
Invalid Flags
$ ike-scan -M --hdrflags=255 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 8 (INVALID-FLAGS)
HDR=(CKY-R=7cc6bd71888f88bc, msgid=b4d315fc)
Invalid Protocol
$ ike-scan -M --protocol=2 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 10 (INVALID-PROTOCOL-ID)
HDR=(CKY-R=e85ced994f2b8cb7, msgid=c7d38cc7)
Invalid SPI
$ ike-scan -M --spisize=32 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=2fd2c9397adba821)
SA=(SPI=6d39f4ab731f0288187685c04c52bc00bb9d1f9e7107602037015b732a77a83e Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
Non-Zero Reserved Fields
$ ike-scan -M --mbz=255 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=84180cb3e3d85ca6)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
NAT Traversal
By default, IBM AIX does not respond to NAT Traversal encapsulated requests.
It supports NAT Traversal because it listens on UDP port 4500 (observed by netstat -na) and will respond to the NAT Traversal Vendor ID. However, it needs ENABLE_IPSEC_NAT_TRAVERSAL to be specified in /etc/isakmpd.conf before it will respond to NAT traversal encapsulated requests.
When NAT traversal is enabled, it will respond to NAT Traversal encapsulated requests as shown below:
$ ike-scan -M --nat-t 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Main Mode Handshake returned
HDR=(CKY-R=9e9ea282dba112ed)
SA=(Enc=DES Hash=MD5 Auth=PSK Group=1:modp768 LifeType=Seconds LifeDuration(4)=0x00007080)
IVEv2
IBM AIX does not support IKEv2 as of 5L version 5.3.
It responds to IKEv2 with INVALID-MAJOR-VERSION as shown below:
$ ike-scan -M --ikev2 192.168.124.156
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
192.168.124.156 Notify message 5 (INVALID-MAJOR-VERSION)
HDR=(CKY-R=b8a2f3e2e260aea4, msgid=2df78af0)
Remote Access VPN Client
There is no separate Remote Access VPN client for IBM AIX, although generic clients like SafeNet should work.
Other Interesting Behaviour
Default Configuration
/etc/isakmdp.conf
# @(#)54 1.11 src/bos/usr/sbin/isakmp/main/isakmpd.conf, ike_isakmpd, ike530 3/22/04 14:26:33 # # /etc/isakmdp.conf - IKE configuration file # ########################################################### # # # This file can be used to configure the following. # # Logging: # 1) The log config for the IKE daemons. # isakmpd behavior: # 2) whether isakmpd will accept a main mode negotiation from an unknown peer # CRL behavior: # 3) The SOCKS4 server information to be used when the CRL is to # be fetched using the HTTP protocol. # 4) The LDAP server information to be used when the CRL is to # be fetched from a LDAP server. # 5) To specify the CRL fetch order, whether HTTP is queried first # or LDAP, when both servers are configured. # 6) To allow multiple login sessions with same ID. # 7) To enable IPsec NAT traversal # 8) To specify IPsec NAT keepalive interval # # Note : The comment lines start with a '#' symbol. # # 1) Log config # # The syntax for this option is simply a log level keyword. # # The IKE daemons use 4 levels of logging. They are: # # 1) none = No logging. This is the default. # 2) error = Log when there are protocol/API errors. # 3) isakmp_events = Logs IKE protocol events and errors. # 4) information = Logs protocol/implementation information. # This level should be used when debugging a # problem. # # 2) Unrecognized IP address negotiation # # The syntax for this option is: # # MAIN_MODE_REQUIRES_IP= YES or NO # # If this is set to YES, then in order for this host to accept an # incoming main mode tunnel, the local IKE database must contain # an IP address for both phase 1 tunnel endpoints (whether as the # primary ID or as an optional IP address associated with some # other ID type). If this is set to NO, this host may accept an # incoming main mode connection even if the IKE database does not # specify IP addresses for its phase 1 endpoints, as long as # certificate-based authentication is used. This allows a host # with a dynamically-assigned IP address to initiate a main mode # tunnel to this machine. # # If this parameter is not specified, the default value is NO. # # 3) SOCKS4 server configuration # # The syntax for this option is: # # mnemonic= value # # where mnemonic can be: # # SOCKS4_SERVER= specifies the server name # SOCKS4_PORTNUM= specifies the socks server port number # SOCKS4_USERID= user id # # The SOCKS4_PORTNUM mnemonic is optional. If not specified, # the default socks server port value of 1080 will be used. The # port value is used when the SOCKS server communicates with # the HTTP server. # # 4) LDAP server configuration # # The syntax for this option is: # # mnemonic= value # # where mnemonic can be: # # LDAP_SERVER= specifies the LDAP server name # LDAP_VERSION= the version of the LDAP server. (can be 2 or 3) # LDAP_SERVERPORT= the LDAP server port number # LDAP_SEARCHTIME= client search timeout value # # 5) CRL Fetch Order # # The syntax for this option is: # # CRL_FETCH_ORDER= protocol1, protocol2 # # where protocol# can be 'HTTP' or 'LDAP'. # # The CRL_FETCH_ORDER mnemonic is optional. The default fetch order # will be HTTP first, then LDAP, depending on if both HTTP and LDAP # servers are configured. # # 6) Allow Multiple Logins # You can allow multiple login sessions with the same ID by # specifying following text: # # MULTI_LOGIN_OK # # 7) Enable IPsec NAT Traversal # You can enable IPsec NAT Traveral and UDP encapsulation functionality # by specifying following text: # # ENABLE_IPSEC_NAT_TRAVERSAL # # 8) NAT Keep Alive Interval # # The syntax for this option is: # # NAT_KEEPALIVE_INTERVAL = keepalive interval value (seconds) # # The NAT_KEEPALIVE_INTERVAL is optional. The default value is 20 seconds. # ########################################################################## #none SOCKS4_SERVER= SOCKS4_PORTNUM=1080 SOCKS4_USERID= LDAP_SERVER= LDAP_VERSION=2 LDAP_SERVERPORT=389 LDAP_SEARCHTIME=10 CRL_FETCH_ORDER=HTTP,LDAP MAIN_MODE_REQUIRES_IP=NO
Discovered Vulnerabilities
Misc Notes
It only seems to support gateway-to-gateway mode, therefore the testing system needs to be configured as the remote gateway IP.
Example IKE configuration displayed with ikedb -g:
<?xml version="1.0"?>
<AIX_VPN
Version="2.0">
<IKEProtection
IKE_Role="Both"
IKE_XCHGMode="Main"
IKE_KeyOverlap="15"
IKE_Flags_UseCRL="No"
IKE_ProtectionName="test_TRANSFORM"
IKE_ResponderKeyRefreshMaxKB="1000000"
IKE_ResponderKeyRefreshMinKB="50"
IKE_ResponderKeyRefreshMaxMinutes="2880"
IKE_ResponderKeyRefreshMinMinutes="2">
<IKETransform
IKE_Hash="MD5"
IKE_DHGroup="1"
IKE_Encryption="DES-CBC"
IKE_KeyRefreshMinutes="480"
IKE_AuthenticationMethod="Preshared_key"/>
</IKEProtection>
<IKETunnel
IKE_TunnelName="test"
IKE_ProtectionRef="test_TRANSFORM"
IKE_Flags_AutoStart="Yes"
IKE_Flags_MakeRuleWithOptionalIP="No">
<IKELocalIdentity>
<IPV4_Address
Value="192.168.124.156"/>
</IKELocalIdentity>
<IKERemoteIdentity>
<IPV4_Address
Value="192.168.124.7"/>
</IKERemoteIdentity>
</IKETunnel>
<IKEPresharedKey
Value="changeslatter"
Format="ASCII">
<IKEPresharedRemoteID>
<PK_User_FQDN
Value="royhills@hotmail.com"/>
</IKEPresharedRemoteID>
</IKEPresharedKey>
<IKEPresharedKey
Value="changeslatter"
Format="ASCII">
<IKEPresharedRemoteID>
<PK_IPV4_Address
Value="192.168.124.7"/>
</IKEPresharedRemoteID>
</IKEPresharedKey>
<IPSecProposal
IPSec_ProposalName="test_PROPOSAL">
<IPSecESPProtocol
ESP_Encryption="ESP_DES"
ESP_KeyRefreshKB="2880"
ESP_Authentication="HMAC-MD5"
ESP_EncapsulationMode="Tunnel"
ESP_KeyRefreshMinutes="480"/>
</IPSecProposal>
<IPSecProtection
IPSec_Role="Both"
IPSec_KeyOverlap="15"
IPSec_ProposalRefs="test_PROPOSAL "
IPSec_ProtectionName="test_POLICY"
IPSec_InitiatorDHGroup="0"
IPSec_ResponderDHGroup="NO_PFS GROUP_1 GROUP_2 GROUP_5"
IPSec_Flags_UseLifeSize="No"
IPSec_Flags_UseCommitBit="No"
IPSec_ResponderKeyRefreshMaxKB="1000000"
IPSec_ResponderKeyRefreshMinKB="50"
IPSec_ResponderKeyRefreshMaxMinutes="60"
IPSec_ResponderKeyRefreshMinMinutes="2"/>
<IPSecTunnel
IKE_TunnelName="test"
IPSec_TunnelName="test_2"
IPSec_ProtectionRef="test_POLICY"
IPSec_Flags_OnDemand="Yes"
IPSec_Flags_AutoStart="Yes">
<IPSecLocalIdentity>
<IPV4_Address
Value="192.168.124.156"/>
</IPSecLocalIdentity>
<IPSecRemoteIdentity>
<IPV4_Address
Value="192.168.124.7"/>
</IPSecRemoteIdentity>
</IPSecTunnel>
</AIX_VPN>